
Google researchers stated on Wednesday they have joined a Barcelona, Spain-based IT firm to the sale of superior program frameworks that exploit vulnerabilities in Chrome, Firefox, and Home windows Defender.
Variston IT expenditures alone as a service provider of tailor-built Info safety alternatives, which include technological innovation for embedded SCADA (supervisory regulate and info acquisition) and World wide web of Things integrators, tailor made stability patches for proprietary units, instruments for facts discovery, security coaching, and the progress of safe protocols for embedded gadgets. In accordance to a report from Google’s Menace Evaluation Group, Variston sells another products not outlined on its web site: application frameworks that present every thing a shopper desires to surreptitiously put in malware on devices they want to spy on.
Researchers Clement Lecigne and Benoit Sevens reported the exploit frameworks ended up used to exploit n-working day vulnerabilities, which are those people that have been patched just lately adequate that some targets have not but put in them. Proof suggests, they included, that the frameworks were also made use of when the vulnerabilities ended up zero-times. The scientists are disclosing their results in an try to disrupt the marketplace for spy ware, which they said is booming and poses a risk to different groups.
“TAG’s analysis underscores that the business surveillance market is flourishing and has expanded appreciably in recent several years, generating threat for Web customers close to the globe,” they wrote. “Commercial spy ware places state-of-the-art surveillance capabilities in the hands of governments who use them to spy on journalists, human rights activists, political opposition, and dissidents.”
The researchers went on to catalog the frameworks, which they acquired from an anonymous resource as a result of Google’s Chrome bug reporting plan. Each 1 arrived with instructions and an archive containing the resource code. The frameworks arrived with the names Heliconia Sounds, Heliconia Soft, and Information. The frameworks contained “mature supply code capable of deploying exploits for Chrome, Home windows Defender, and Firefox” respectively.
Provided in the Heliconia Sounds framework was code for cleansing up binary documents ahead of they are generated by the framework to assure they don’t consist of strings that could incriminate the developers. As the picture of the cleaning script demonstrates, the checklist of undesirable strings provided “Variston.”
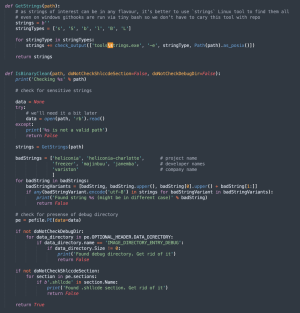
Officers from Variston didn’t respond to an e-mail looking for remark for this publish.
The frameworks exploited vulnerabilities that Google, Microsoft, and Firefox preset in 2021 and 2022. Heliconia Sounds provided each an exploit for the Chrome renderer, together with an exploit for escaping the Chrome stability sandbox, which is created to maintain untrusted code contained in a protected surroundings that simply cannot access delicate components of an working method. For the reason that the vulnerabilities ended up uncovered internally, there are no CVE designations.
Heliconia Sounds could be configured by the purchaser to established issues like the optimum amount of periods to serve the exploits, an expiration day, and rules specifying when a customer really should be viewed as a valid focus on.
Heliconia Comfortable bundled a booby-trapped PDF file that exploited CVE-2021-42298, a bug in the JavaScript motor of Microsoft Defender Malware Protection that was preset in November 2021. Basically sending an individual the doc was adequate to gain coveted technique privileges on Home windows due to the fact Home windows Defender immediately scanned incoming files.
The Information framework contained a completely documented exploit chain for Firefox operating on Home windows and Linux. It exploits CVE-2022-26485, a use-just after-absolutely free vulnerability that Firefox mounted past March. The scientists reported Documents probably exploited the code-execution vulnerability given that at the very least 2019, extensive prior to it was publicly identified or patched. It labored versus Firefox variations 64 to 68. The sandbox escape Data files relied on was preset in 2019.
The researchers painted a photo of an exploit sector that’s significantly out of handle. They wrote:
TAG’s investigation has proven the proliferation of commercial surveillance and the extent to which business adware suppliers have produced capabilities that were earlier only available to governments with deep pockets and specialized expertise. The advancement of the spy ware industry places users at chance and can make the Net fewer protected, and when surveillance technologies may well be legal below nationwide or global regulations, they are generally used in unsafe ways to conduct electronic espionage versus a variety of teams. These abuses signify a severe possibility to on-line safety which is why Google and TAG will continue to acquire motion against, and publish study about, the industrial spyware market.
Variston joins the ranks of other exploit sellers, including NSO Group, Hacking Workforce, Accuvant, and Candiru.








