
The document-vying distributed denial-of-provider assaults preserve coming, with two mitigation expert services reporting they encountered some of the major information bombardments at any time by risk actors whose ways and procedures are regularly evolving.
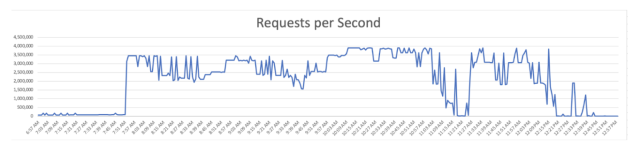
On Monday, Imperva explained it defended a shopper from an attack that lasted more than four hrs and peaked at more than 3.9 million requests for every 2nd (RPS).
Imperva
In all, the attackers directed 25.3 billion requests at the concentrate on with an ordinary price of 1.8 million RPS. When DDoSes exceeding 1 million RPS are expanding significantly widespread, they typically occur in shorter bursts that evaluate in seconds or a several minutes at most.
Imperva
A significant botnet
“[The] attackers made use of HTTP/2 multiplexing, or combining several packets into one, to ship multiple requests at as soon as about person connections,” Imperva’s Gabi Stapel wrote. “This method can carry servers down working with a limited range of means, and this kind of attacks are exceptionally tough to detect.”
Stapel claimed that the assault probably would have peaked at an even higher level experienced it not been countered by Akamai’s mitigation company. The focus on of the DDoS was a Chinese telecommunications company that has arrive below assault ahead of.
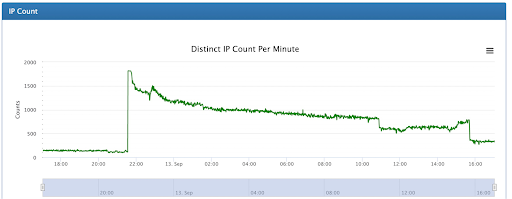
The assault originated with a botnet of routers, stability cameras, and hacked servers connected to pretty much 170,000 distinct IP addresses. The IP addresses were being situated in more than 180 nations, with the US, Indonesia, and Brazil becoming the most frequent. Some of the botnet gadgets had been hosted on several community clouds, together with people offered by security services providers.
The arms race proceeds
Previous week, Akamai claimed it not long ago defended a client in Japanese Europe in opposition to a history-environment assault of 704.8 million packets for every next. The similar buyer, Akamai claimed, experienced by now established a history in July when it skilled a 659.6 Mpps DDoS from the identical menace actor.
The most recent attack sprayed packets at six worldwide areas the concentrate on maintains, from Europe to North The usa.
“The attackers’ command and manage method had no hold off in activating the multidestination attack, which escalated in 60 seconds from 100 to 1,813 IPs active for each moment,” Akamai’s Craig Sparling wrote. “All those IPs had been distribute throughout eight distinct subnets in six distinctive spots. An assault this seriously dispersed could drown an underprepared protection crew in alerts, creating it challenging to evaluate the severity and scope of the intrusion, permit by itself battle the attack.”
Akamai
DDoS attacks can be calculated in many ways, including by the quantity of data, the range of packets, or the quantity of requests despatched each second. The current data include 3.4 terabits for every 2nd for volumetric DDoSes—which attempt to take in all bandwidth out there to the target—809 million packets for each next and 17.2 million RPS. The latter two documents measure the energy of software-layer attacks, which try to exhaust the computing sources of a target’s infrastructure.
The ever-raising numbers underscore the arms race amongst attackers and defenders as each and every endeavor to outdo the other. These file-location quantities are not probably to halt any time before long.








